Which Box Testing Is Best Used With Vulnerability Assessments
Reconnaissance in information security is used for ___. Which of the following is best used for penetration testing.

White Box Testing What Is Types Techniques Example
Conversely these two should be combined together to yield better results.

. White box testing provides the penetration testers information about the target network before they start their work. Identifying the number of security flaws within the system. White box testing fills all the blind spots in security testing which are skipped in gray box or black box too.
B White Box Testing. Grey Box Testing Grey Box Testing Which of the following is best used with vulnerability assessments. Select the appropriate answer from below options.
Grey-box assessments are often used when people are confused about the difference between a Penetration Test and a vulnerability assessment. White Box Testing White Box Testing The type of security assessment that aims to test the organizations detection and response capabilities Red. Grey Box Testing Black Box Testing White Box Testing 1 See answer Add answer 5 pts Advertisement jyotikawade2020 is waiting for your help.
This information can include such details as IP addresses network infrastructure schematics and the protocols used plus the source code. SanerNow vulnerability management tool provides automated scans for your IT. It is very helpful to even do review the quality outcome by source code development vendor or team.
A Grey Box Testing. Advertisement Still have questions. Q20 Which of the following is best used with vulnerability assessments.
This information can include such details as IP addresses network infrastructure schematics and the protocols used plus the source code. White box testing provides the penetration testers information about the target network before they start their work. Further penetration of the.
Which of the following is best used with vulnerability assessments. Quantifying the systems available services. Best Used When.
Which of the following is best used for penetration testing. Security Assessment MCQ Questions Answers. Which of the following is best used with vulnerability assessments.
White Box Testing B. Our customers often ask us what the best frequency of testing is. Choose the correct option from below list 1Grey Box Testing 2White Box Testing 3Black Box Testing Answer-3Black Box Testing.
Measuring the systems integrity in the presence of failure. Ad Find Vulnerability Assessment Tool. Add your answer and earn points.
For example it can cover issues like hardcoded account numbers or email ids used for transactions logics. Correct answer of the above question is. Ad Protect Your Business by Highly Securing Your Internet of Things.
Black Box Testing C. White-box penetration testing provides a comprehensive assessment of both internal and external vulnerabilities making it the best choice for calculation testing. In black box testing a vulnerability assessment is carried out identifying entry points for an attacker.
VAPT is often misunderstood as two different types of testing techniques. Many settle for yearly assessments or when major changes are made to applications or infrastructures. Vulnerability Assessment and Penetration Testing VAPT is a testing process to find security bugs within a software program webmobile or a computer network.
Search For Vulnerability Assessment Tool Now. Answer 50 5 6 jai696 While all 3 are useful at assessing vulnerabilities Grey Box Testing is ideal to balance time cost and impact. Determining the probability that the system functions safely during any time period.
Select the appropriate answer from below options. Ad SanerNow is among the best vulnerability management tools that can help an organization. However it is becoming more and more.
C Black Box Testing. White-box assessments are best used with vulnerability assessments because you want to find as many issues as possible regardless of how the tester came to discover them. The close relationship between white-box pentesters and developers provides a high level of system knowledge but may affect testers behaviors since they operate based on knowledge not.
The OWASP Zed Attack Proxy ZAP is an easy to use integrated penetration testing tool for finding vulnerabilities in web applicationsIt is designed to be used by people with a wide range of.
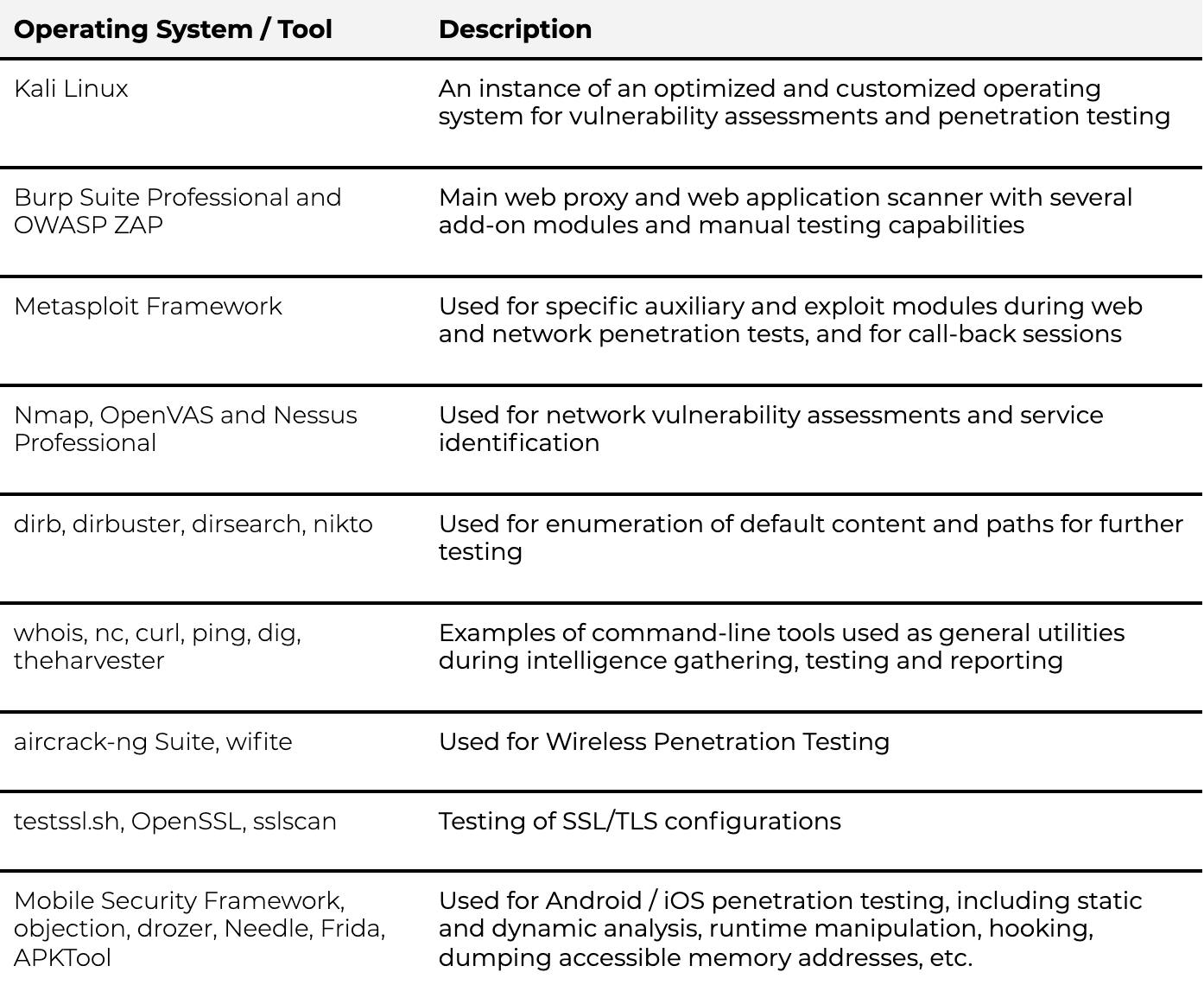
Pentesting Tools Resources To Get You Started
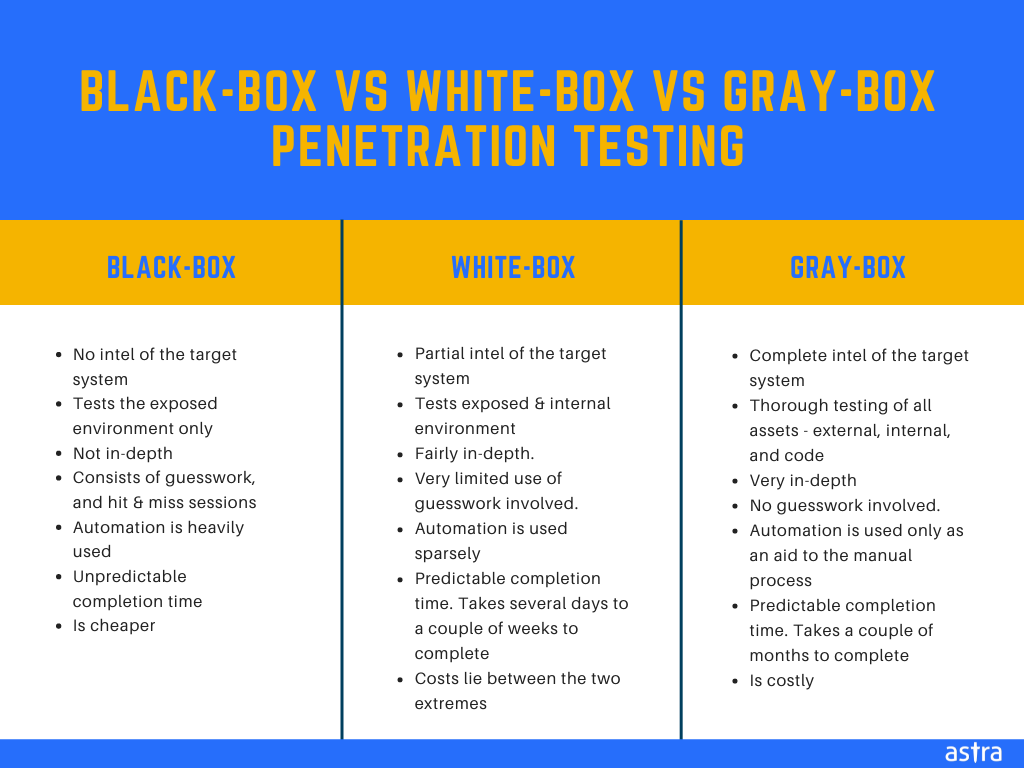
Black Box Penetration Testing Benefits Drawbacks Techniques Tools
Introduction To Vulnerability Assessment And Penetration Testing Neurones It Asia

13 Best Vapt Tools Ranked For 2022 Paid Free Trials Open Source

What Is A Vulnerability Assessment A Detailed Guide Testbytes
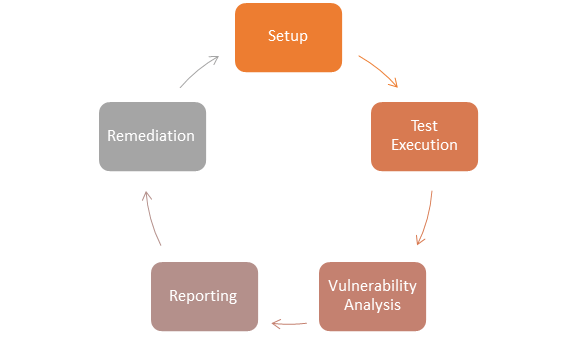
What Is Vulnerability Assessment Testing Process Vapt Scan Tool
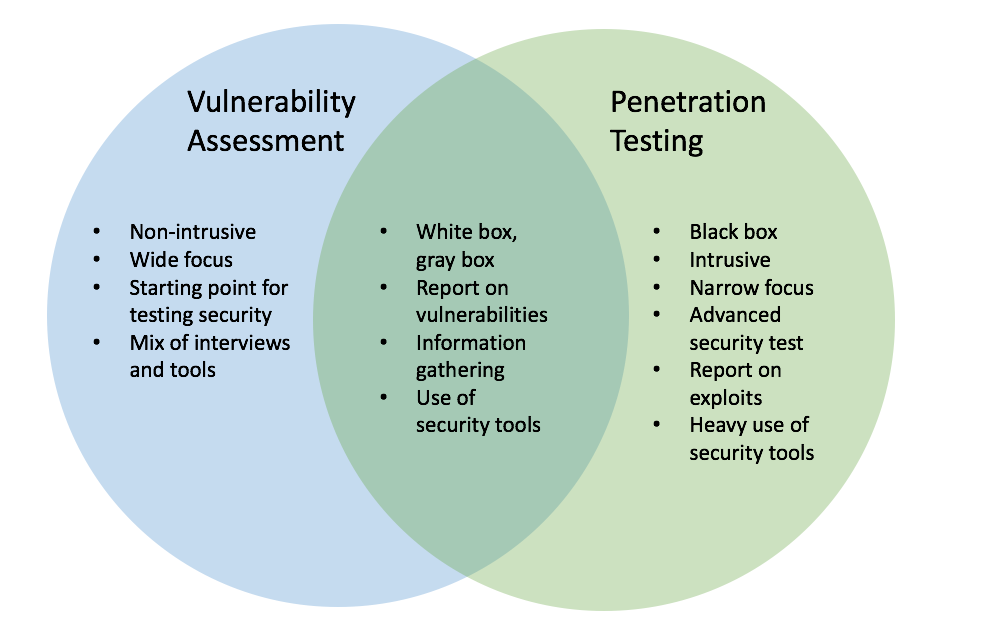
It Vulnerability Assessments Vs Penetration Testing In Braintree Ma

What Is A Vulnerability Assessment A Detailed Guide Testbytes

Black Box Penetration Testing Benefits Drawbacks Techniques Tools
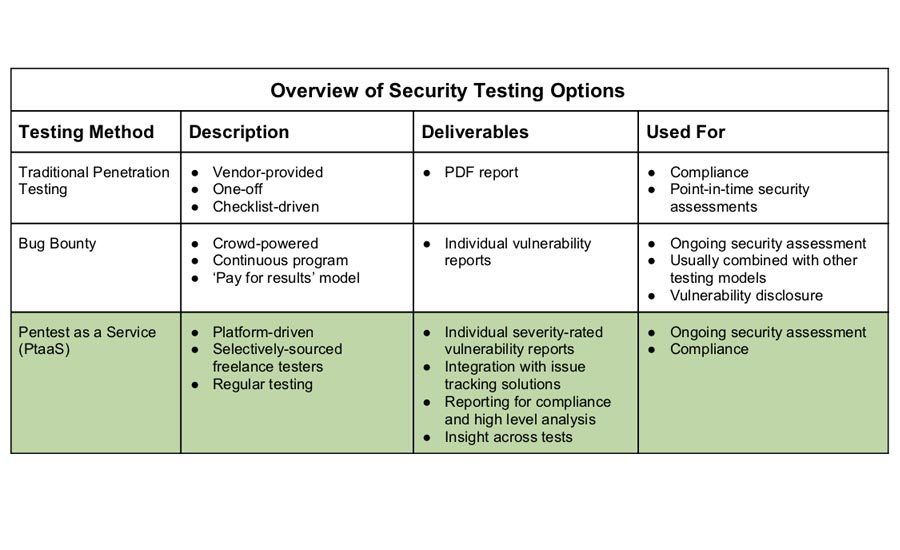
A Comprehensive Guide To Building A Pentest Program 2020 08 17 Security Magazine

Vulnerability Assessment And Penetration Testing Difference

How To Do A Full Network Vulnerability Assessment With Pentest Tools Com Pentest Tools Com Blog
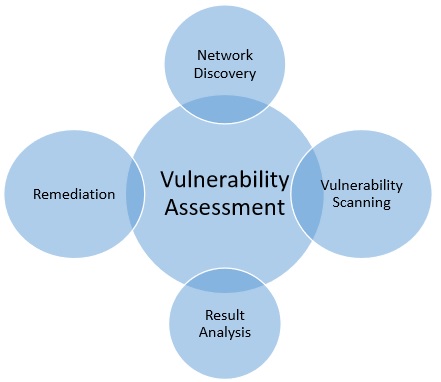
Penetration Testing Quick Guide

What Is Vulnerability Assessment Testing Process Vapt Scan Tool
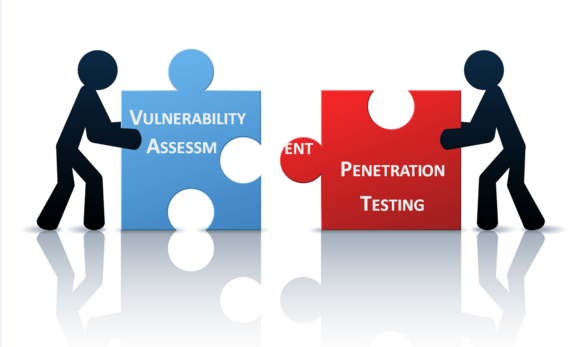
What Is Vulnerability Assessment Testing Process Vapt Scan Tool

19 Powerful Penetration Testing Tools Used By Pros In 2022
Introduction To Vulnerability Assessment And Penetration Testing Neurones It Asia
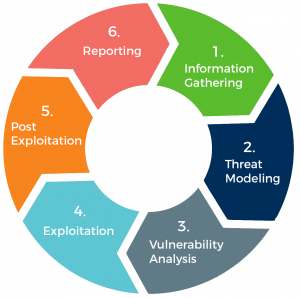
Mobile Application Vulnerability Assessment And Penetration Testing Services Zero2infynite

good blog post!!!!
ReplyDeletecyber security penetration testing training